
I ran into this issue today and sharing for anyone else that may run into the same problem. The scenario is fairly simple, Azure AD Connect synchronizing to Azure AD. All works fine until MFA policies were enabled, and then sync stops working. Running a Sart-ADSyncSyncCycle returns a lot of red, but the basic are:
Start-ADSyncSyncCycle : System.Management.Automation.CmdletInvocationException: System.InvalidOperationException: Showing a modal dialog box or form when the application is not running in UserInteractive mode is not a valid operation. Specify the ServiceNotification or defaultDesktopOnly style to display a notification from a service application.
The Event Log reports Event ID: 906 with the following error message:
GetSecurityToken: unable to retrieve a security token for the provisioning web service (AWS). Showing a modal dialog box or form when the application is not running in UserInteractive mode is not a valid operation. Specify the ServiceNotification or DefaultDesktopOnly style to display a notification from a service application.
The MFA Conditional Access Policy put in place included all users with MFA Trusted IPs excluded from the policy. The computer with AD Connect installed ran in Azure and had a dynamic public IP assigned. The computer shut off overnight (this was a lab) and the next day, after getting a new external IP address, AD Connect quit working.
Once the public IP address changed on the AD Connect server, the AD Connect Sync account was in scope for the MFA policy. That prevented the account from logging in and caused the error.
There are two ways to fix this. First, update the MFA Trusted IPs with the new external IP address. That will exclude the computer from MFA, and things should start working again. At least until that IP changes.
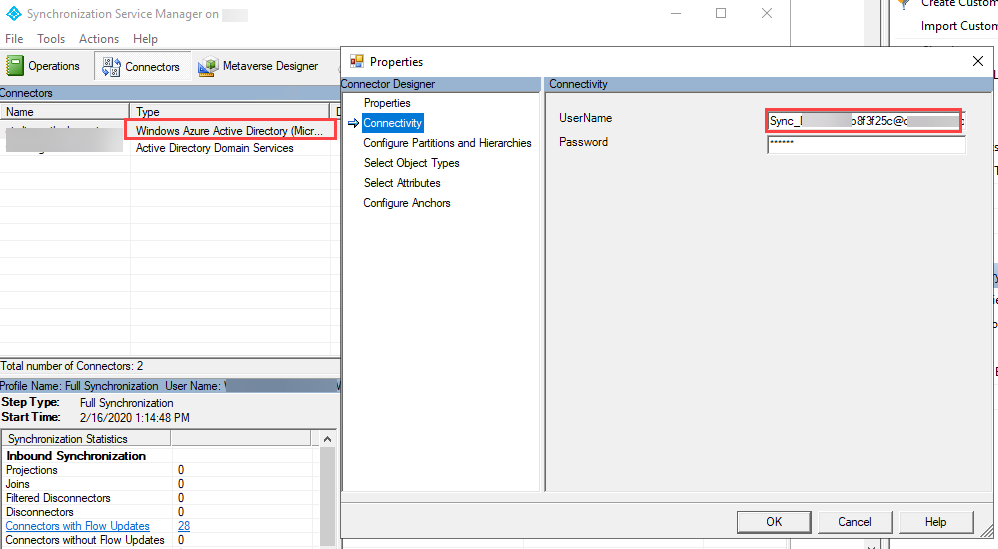
The better option is to exclude the sync account from the MFA policy. Find the account name by going into the AD Connect Synchronization Service Manager and go to Connectors. Find the connector type Windows Azure Active Directory and go to Properties, Connectivity.
Find the account to exclude in the UserName field.
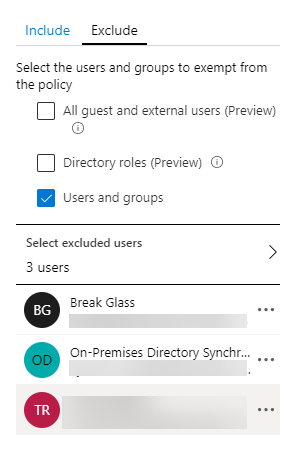
Next, go to the Conditional Access Policy that’s enforcing MFA for your tenant in Azure AD. Go to Users and Groups, and go to the Exclude tab. Under Select users to Exclude, find and add the Sync account used to sync the on-premises directory. Add and save that to the MFA user exclusion.
Making one of these changes fixed the issue. So far, I have only had a problem with the sync account. I’m sure there will be a need to add other automation accounts now that MFA enforcement is on by default.




15 thoughts on “MFA Conditional Access Policy Breaks AD Connect Synchronization”
I have got to be honest, you saved my ass with this one. Thanks!
Thanks Travis, I’m curious why this isn’t something that Microsoft addresses in another way, some warning, or notice even.
Thanks! I suspected something like this!
Great!! Summarize it all. You can include all replies above as mine as well
Thank you for taking the time to post this. Would have been searching for hours if it wasnt for this post.
Glad it helped!
Really helpful. I knew that the MFA rule was likely the culprit, but we thought we had excluded the correct account, so was scratching my head, but it turns out that there were two accounts we needed to exclude.. This really helped.
Good stuff, saved me a lot of time. Much appreciated
THANK YOU!
Travis, next time you are in Towcester England I’ll take you out for a beer!
I’ll let you know next time I’m in the area!
You saved me a lot of headache with this one, thank you Travis! Big fan of your content on YouTube and Udemy.
Thanks, glad it helped!
This helped fix our issue. Thanks so much for sharing!
Thank you!